It’s a good idea to set an IAM access policy for anything that accesses AWS using your account details, I wanted to do this for s3cmd syncing a local directory to an s3 bucket. There are a number of posts on setting up the IAM policy for s3cmd already but none of the examples worked for me, I got a 403 permission denied error when running the s3cmd sync command.
After some digging it turns out that s3cmd now tries to set an ACL on the files it uploads, and this needs to be specifically allowed in the ACL. I’m guessing that it didn’t in the past, hence the now incorrect IAM advice. So here is the new working IAM policy, complete with the s3:PutObjectAcl permission added:
(See jrantil’s comment below on wether s3:ListAllMyBuckets is needed in this instance)
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "Stmt1397834652000",
"Effect": "Allow",
"Action": [
"s3:ListAllMyBuckets"
],
"Resource": [
"arn:aws:s3:::*"
]
},
{
"Sid": "Stmt1397834745000",
"Effect": "Allow",
"Action": [
"s3:ListBucket",
"s3:PutObject",
"s3:PutObjectAcl"
],
"Resource": [
"arn:aws:s3:::bucketname",
"arn:aws:s3:::bucketname/*"
]
}
]
}
Update!
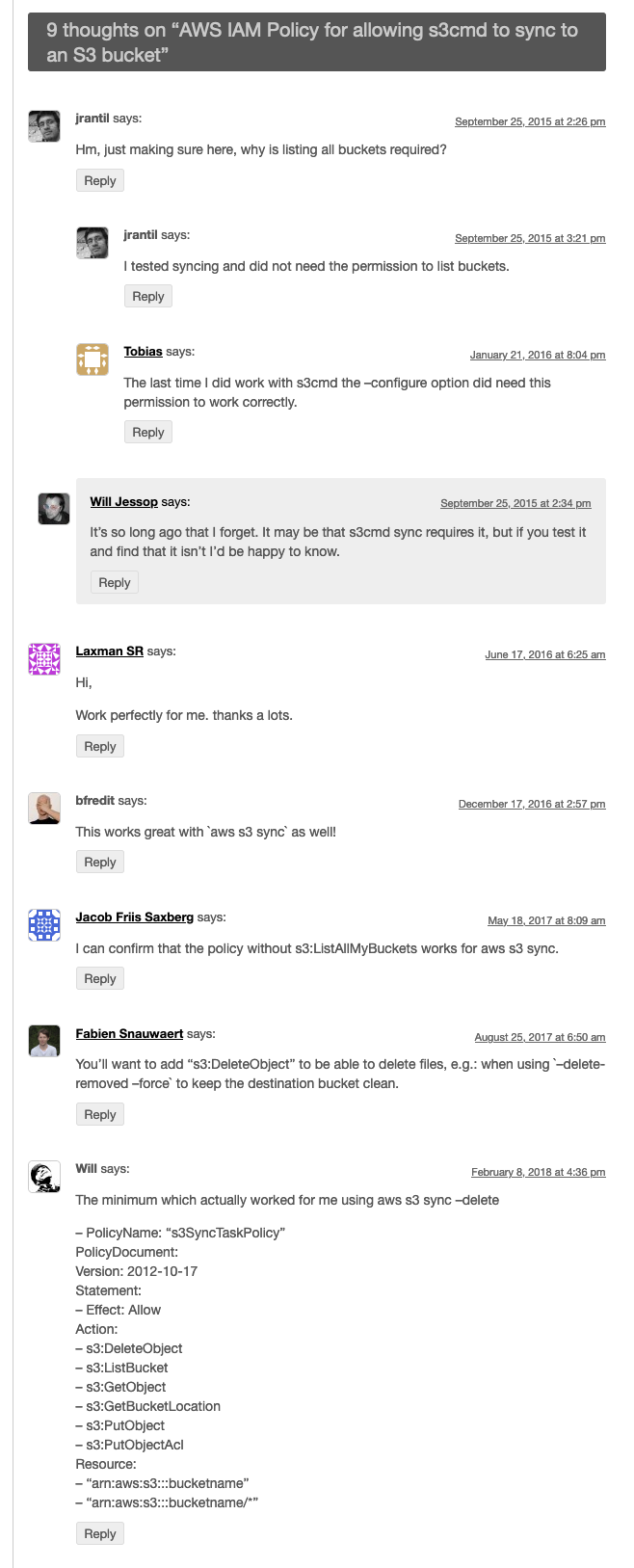
This post was imported from my original blog where there were comments, and these may be relevant to anyone finding this page now: